EXTRA EXTRA! ORDS now supports JSON Web Tokens (JWTs). You can find most of the details in the OAuth PL/SQL Package Reference chapter of the ORDS Developer's Guide.
Why is this in the OAuth chapter?
Apparently, JWTs fall under the purview of the OAuth Working Group, a section of the Internet Engineering Task Force (IETF). Here is a draft of the JWT specification I found. This makes sense; I’ve since relearned that OAuth = Open Authorization 🤦🏻.
ORDS JWT OAUTH parameters
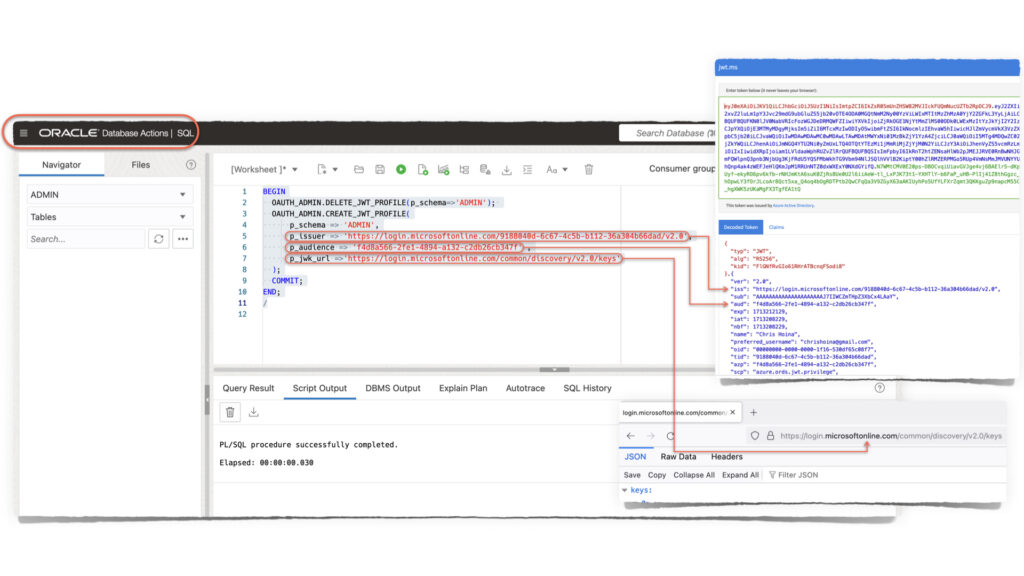
You’ll notice two new procedures in that package: OAUTH.CREATE_JWT_PROFILE and OAUTH.DELETE_JWT_PROFILE. After getting acquainted with them, I wanted to highlight three parameters of the OAUTH.CREATE_JWT_PROFILE procedure:
p_issuerp_audiencep_jwk_url
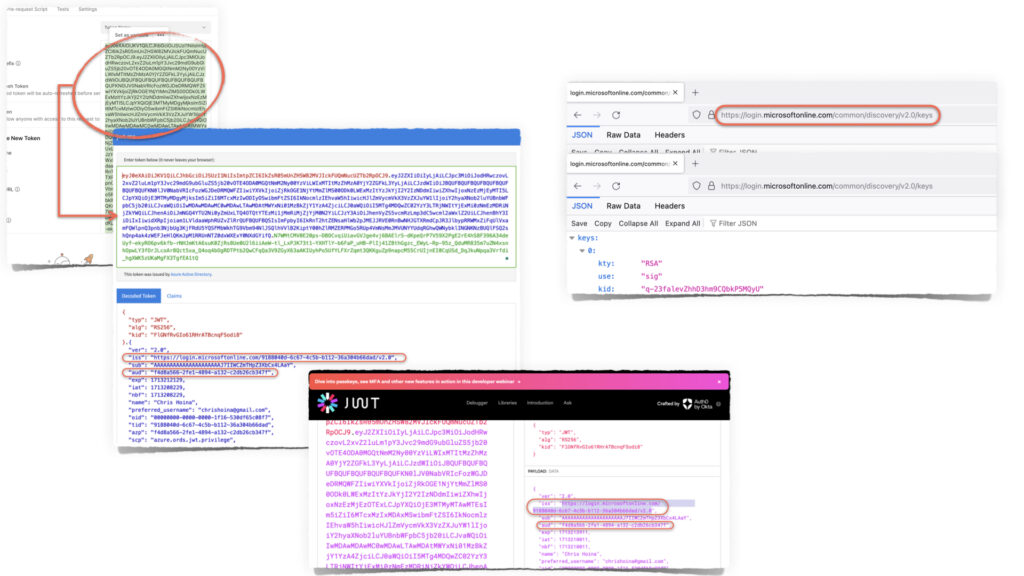
Your JWT issuer (e.g., Microsoft Entra or Oracle Identity Cloud Service) will provide you with these three values required for the OAUTH.CREATE_JWT_PROFILE procedure.
However, they might be referred to by slightly different names. I first noticed this as I set up Microsoft Entra to work with ORDS (below are images taken from a slide deck I’m working on).


Learn more about these parameters.
- About Registered Claim Names (this includes “
iss” and “aud“) - About JSON Web Keys (JWKs)
In fact, I could use some help finding [what we refer to as] the p_jwk_url in the Microsoft Entra dashboard. I'm sure it's there, but I couldn't find it. In case you need it, this is the link that I used.
So, the names are all slightly different. But if I can figure it out, you definitely can.
Decoding JWTs
Once you acquire your JWT, you’ll need a way to decode it so you can use it for testing or development, and you’ll need some of the information for the ORDS profile procedure! Several resources exist, but here is a [non-exhaustive] list I put together:
- the JWT.io debugger
- Microsoft’s JWT debugger
- Comprehensive list of libraries for various languages and frameworks
If you choose to use a web-based decoder, it’ll look like this (paste your Token):


But you might prefer something other than putting your JWT into a browser for decoding.
Homegrown
So, if you’re like me (and didn’t do your research beforehand), you might try to come up with something independently. Something you can run locally.
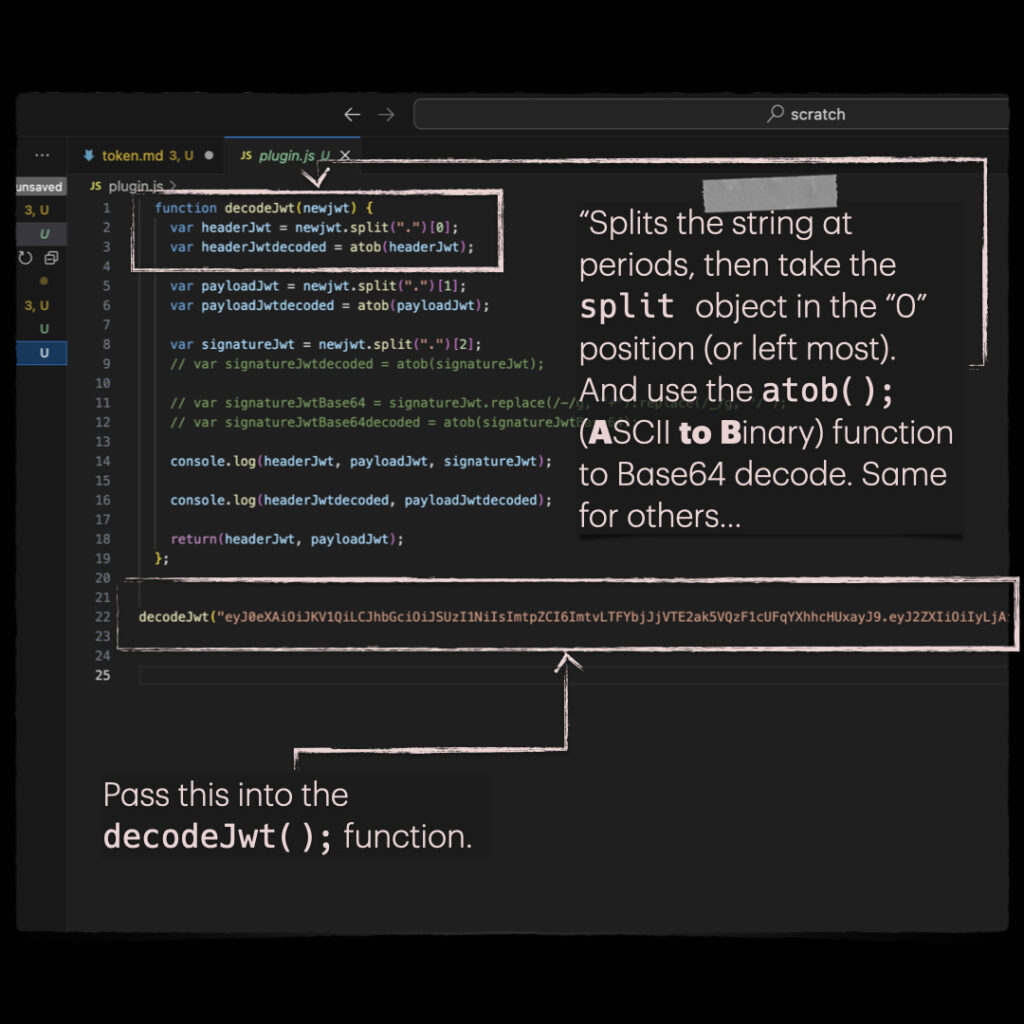
I created a JavaScript function that expects a JWT and “splits” on the periods. From there, Base64 decodes the necessary stuff for you and returns it:
function decodeJwt(newjwt) {
var headerJwt = newjwt.split(".")[0];
var headerJwtdecoded = atob(headerJwt);
var payloadJwt = newjwt.split(".")[1];
var payloadJwtdecoded = atob(payloadJwt);
var signatureJwt = newjwt.split(".")[2];
// var signatureJwtdecoded = atob(signatureJwt);
// var signatureJwtBase64 = signatureJwt.replace(/-/g, "+").replace(/_/g, "/");
// var signatureJwtBase64decoded = atob(signatureJwtBase64);
console.log(headerJwt, payloadJwt, signatureJwt);
console.log(headerJwtdecoded, payloadJwtdecoded);
return(headerJwt, payloadJwt);
};
decodeJwt("Your JWT goes here.");
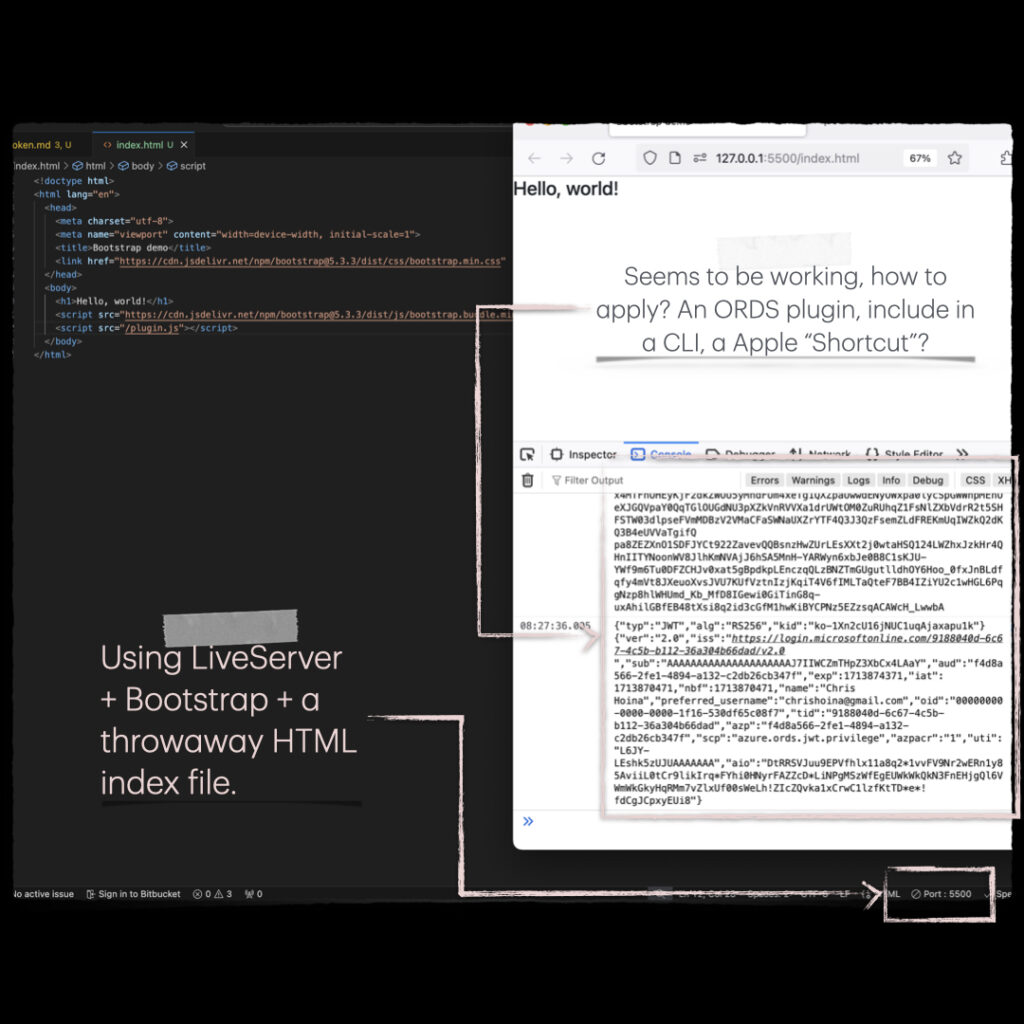
To illustrate how this function works, I took some “boilerplate” HTML from the Bootstrap docs page and spun up a LiveServer in VS Code. I’m also “inspecting” the results from the console.log();. I’m not really sure how far I’ll take this, especially now that I’ve learned about all the existing libraries. But feel free to remix this code!
Thank you for your time 🙇🏻♂️
And that’s all I have to share for today!
If you still need to download and upgrade to the latest ORDS, you can find the.zip file here. Be sure to explore GraalVM, too; you can “unlock” some newer ORDS features by using GraalVM as your primary Java Developer Kit (JDK)!
Follow
And don’t forget to follow, like, subscribe, share, taunt, troll, or stalk me!
