Tag: JSON Web Tokens
-
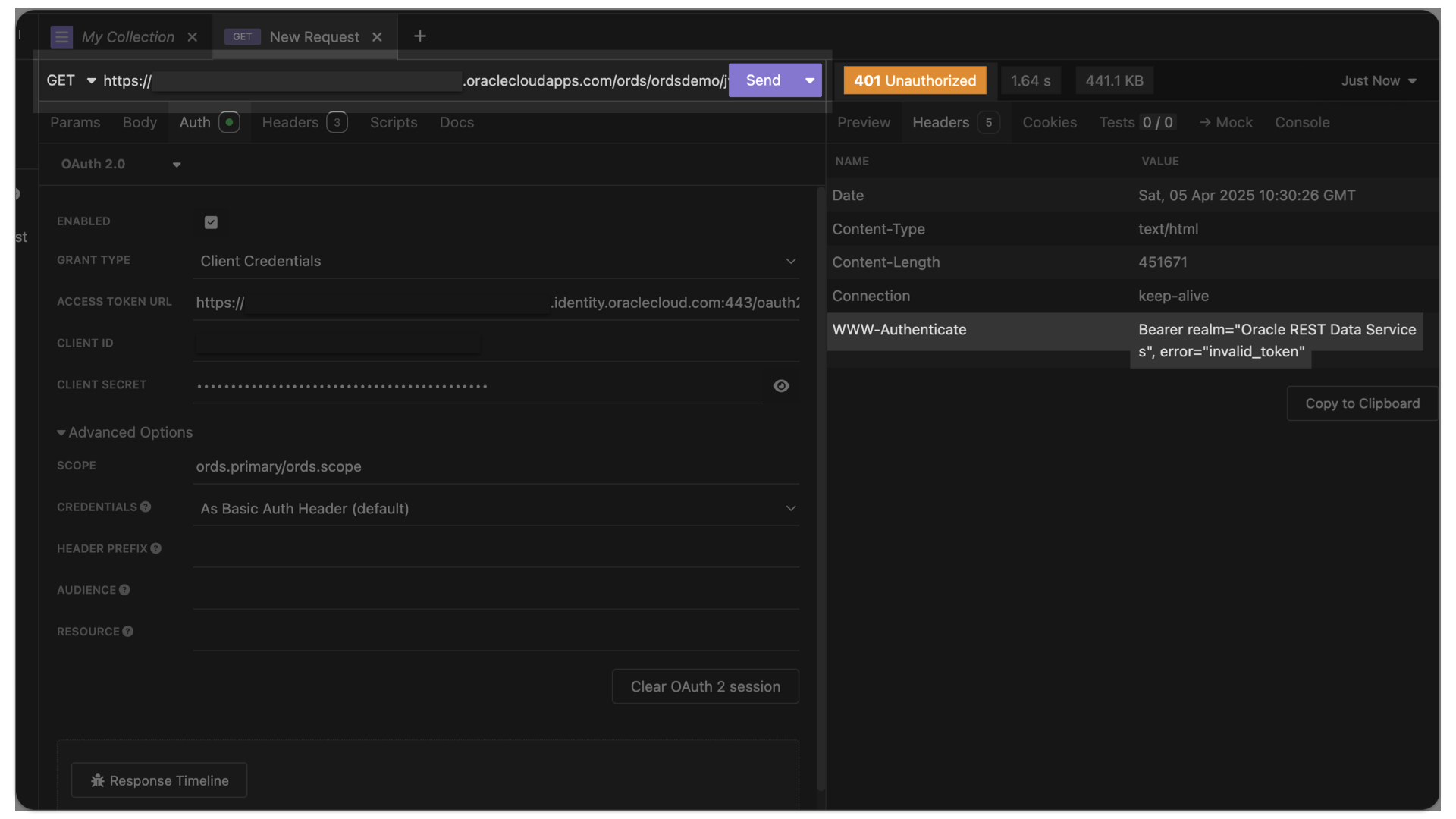
401 Unauthorized invalid_token – troubleshooting Oracle Cloud IAM JWTs with ORDS
Symptoms You are able to request an access token from OCI IAM. Yet, when you issue the subsequent request to your target resource (an ORDS endpoint), you receive the following message (error=”invalid_token”): Actions you’ve taken YET…you still receive this error=”invalid_token” message, it is quite possible that you have not made the JWK URL publically accessible in…
Written by
-
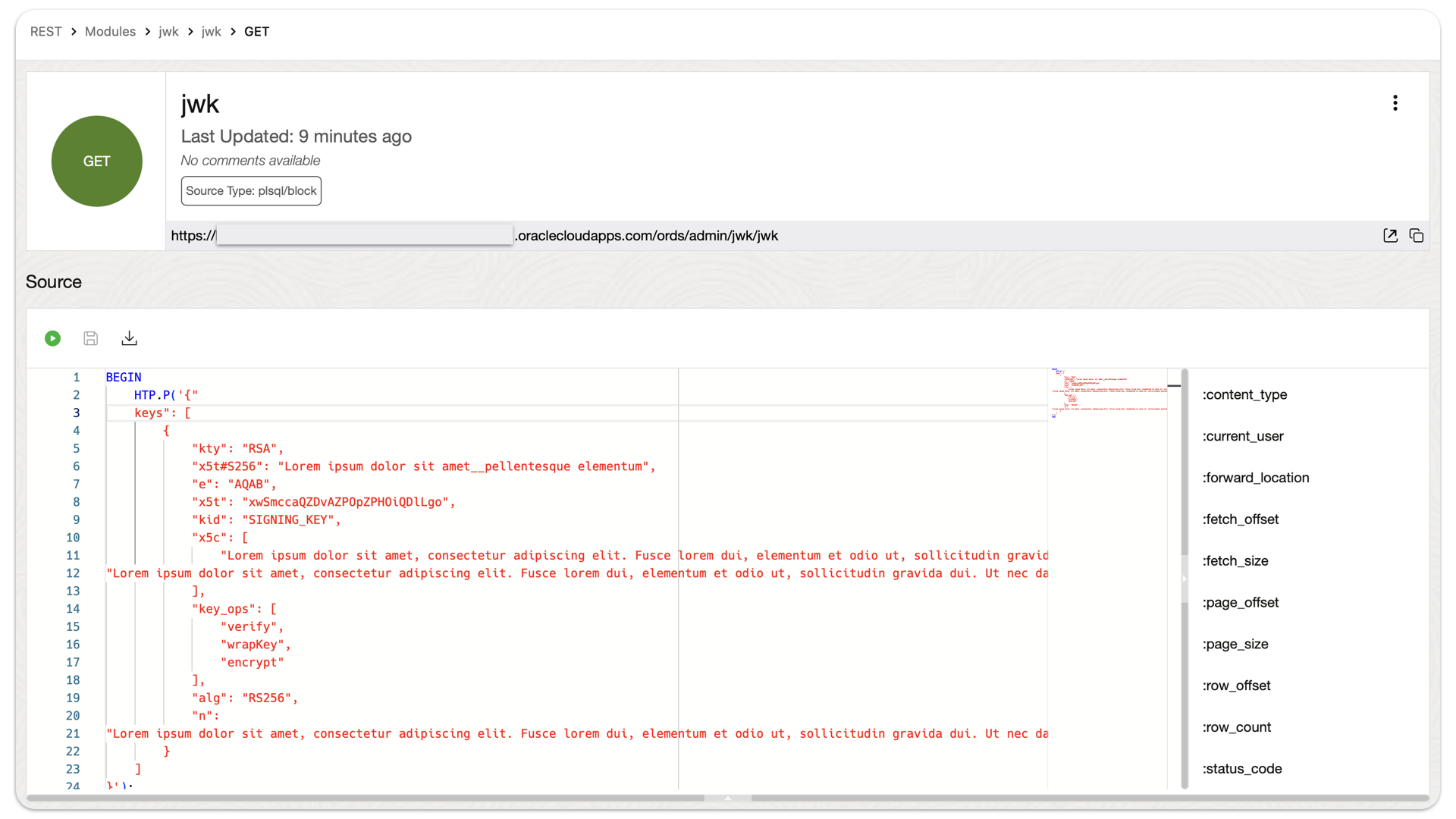
Example: an ORDS API that returns a user-configured JSON object
This actually came about from a Support Request. We were troubleshooting a JWT issue, that had ORDS in the mix. Ultimately, this is looking more and more like a networking issue (maybe something to do with routing rules between the load balancer and the backend server). But in the course of our troubleshooting, we wanted…
Written by
-
Random Access Memories: ORDS and JWTs
EXTRA EXTRA! ORDS now supports JSON Web Tokens (JWTs). You can find most of the details in the OAuth PL/SQL Package Reference chapter of the ORDS Developer’s Guide. ORDS JWT OAUTH parameters You’ll notice two new procedures in that package: OAUTH.CREATE_JWT_PROFILE and OAUTH.DELETE_JWT_PROFILE. After getting acquainted with them, I wanted to highlight three parameters of…
Written by
