Tag: new release
-
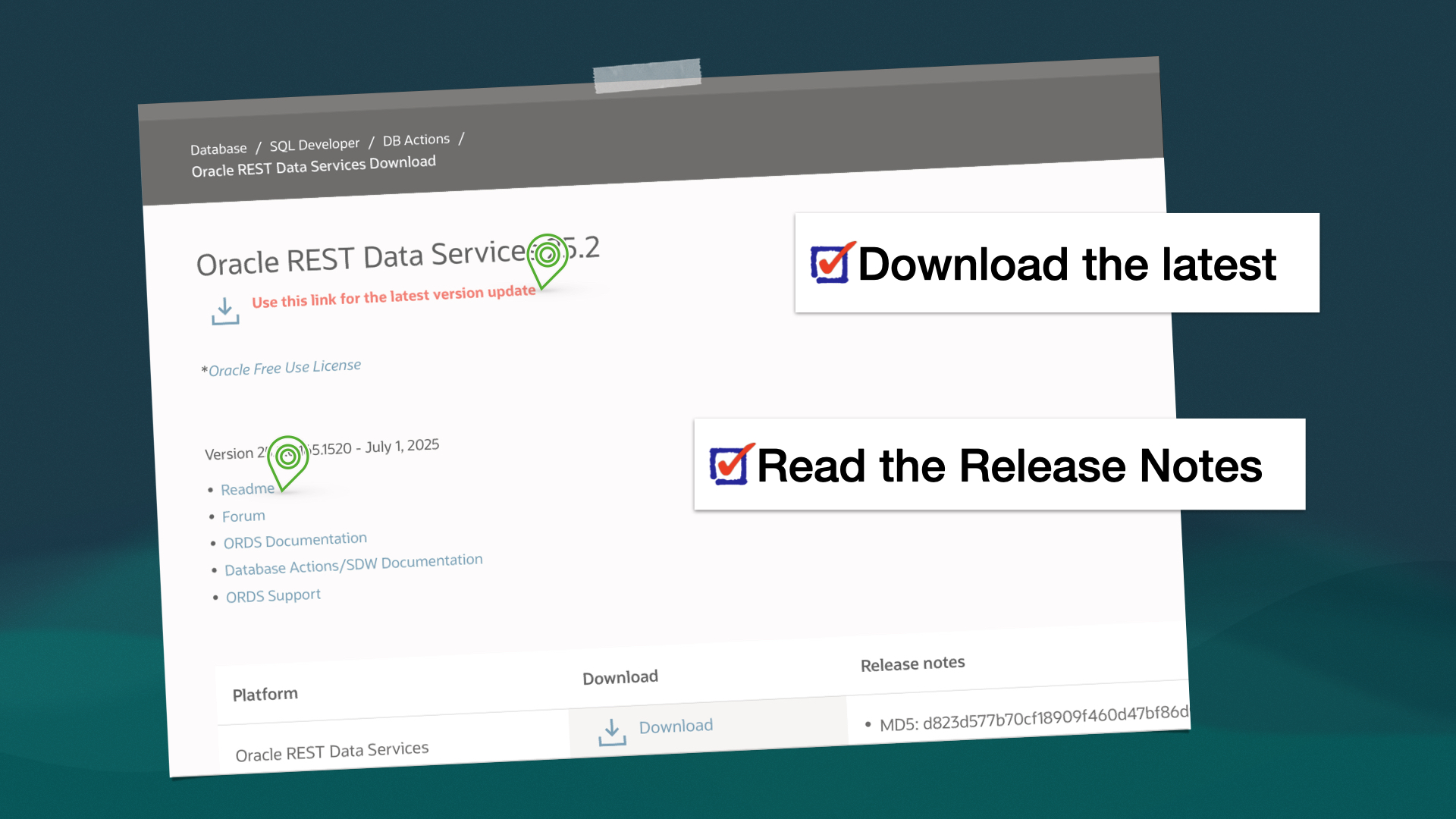
ORDS 25.2 Release Highlights
As always, the complete, official list of enhancements and fixes can be found here. Contained in this brief post are some of the highlights from this latest release. My top enhancements Of the new features the team has published, I’d say these next two are probably going to be the “most sought after” for folks.…
Written by
-
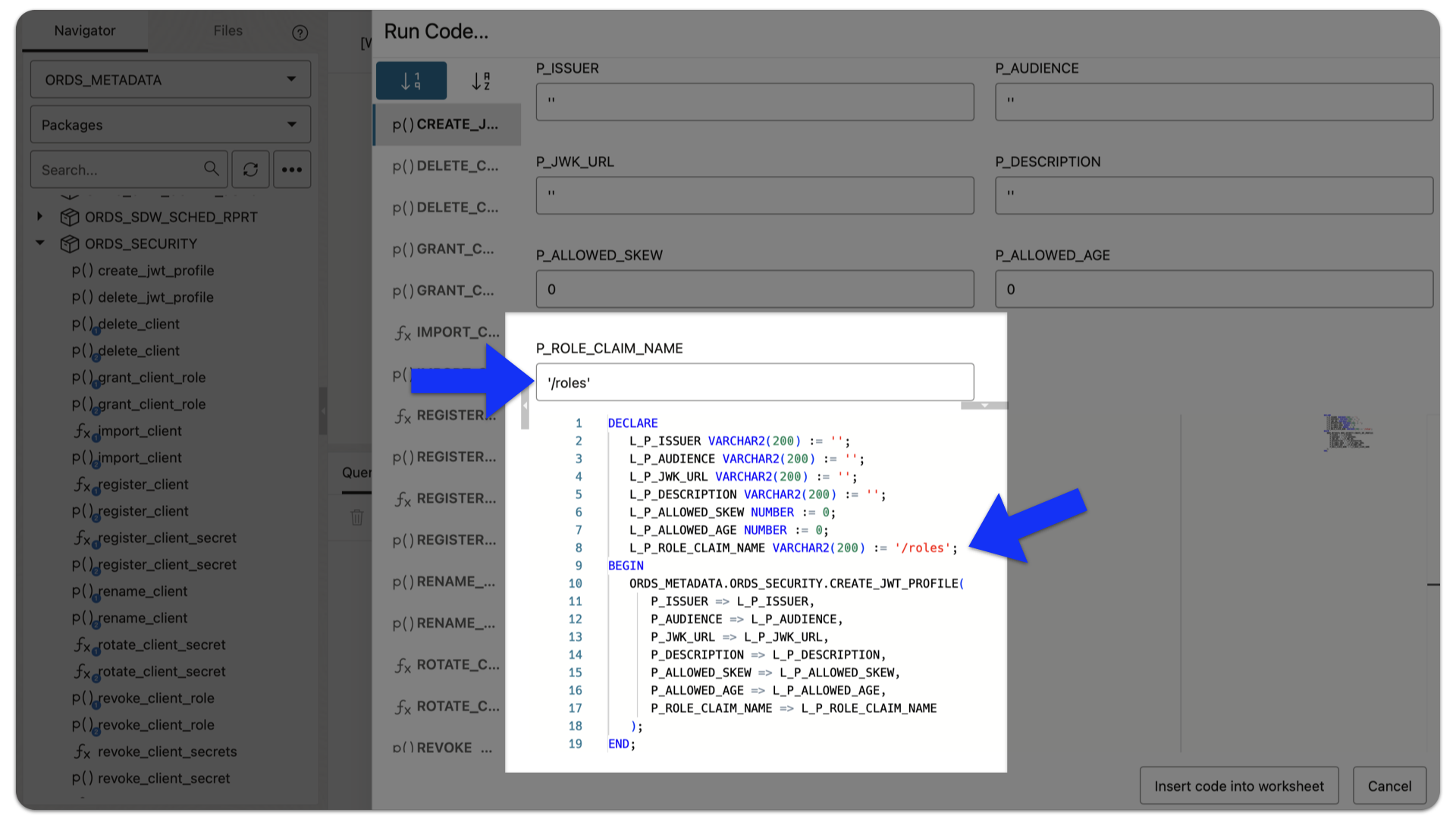
ORDS 25.1 Release Highlights
ORDS 25.1 is now available, here are the highlights 😀 JWT roles-based scopes You are probably well aware of our current JWTs authentication and authorization support. But shortly after releasing this functionality, one of our long-time customers asked us to enhance ORDS JWT Profiles so they could also support roles “claims” (and scopes). So now,…
Written by
-
ORDS 24.4 Release Highlights
So what even is new in ORDS 24.4? How about an abbreviated list of some fan favorites? Pre-Authenticated endpoints Using the new ORDS_PAR PL/SQL package, users can create, revoke, issue and set tokens and token life for specific resources. Your REST-enabled schema will automatically have access to this new feature in 24.4. You can execute…
Written by
-
ORDS 24.2 Release Highlights
NOTE: This can be thought of as a “companion piece” to the official ORDS release notes 🤓. What is new in Oracle REST Data Services 24.2? New HTTPS Response Status Codes In response to various support requests and internal feedback, we’ve expanded on the existing ORDS Status Codes (the current list can be found here)!…
Written by
